Welcome to an updated, comprehensive guide on using Direct Memory Access (DMA) cheats in gaming. Drawing from extensive experience as a staff member on a cheat Discord and a seasoned user of DMA cheats across various games, I’ve compiled a wealth of information to help you navigate this intriguing yet complex landscape.
Understanding DMA Requirements
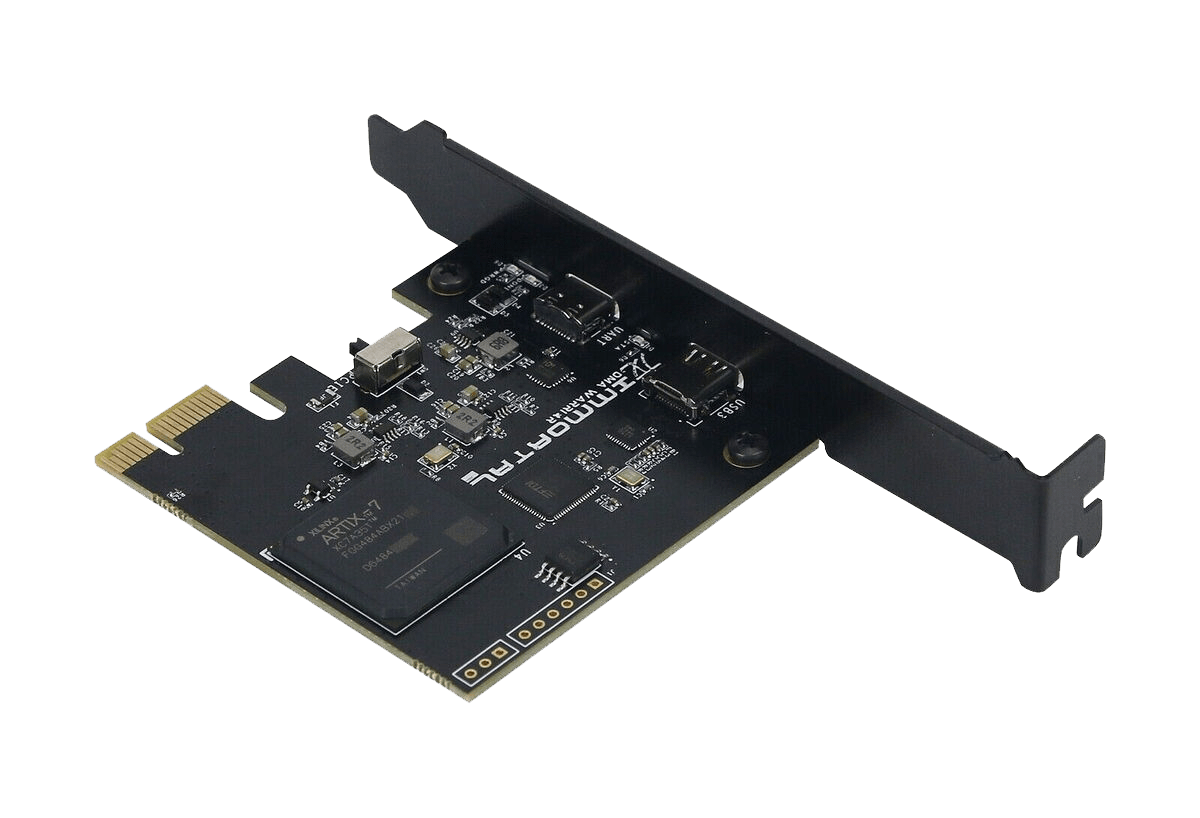
DMA (Direct Memory Access) cards are small boards primarily used for game cheating or forensic analysis. They hold minimal value outside these realms, leading to limited support. The community largely relies on ulfrisk, the developer behind pcileech, for guidance and tools. Here are the essential requirements for owning and using a DMA card:
- Mental Acumen: You’ll need a sharp mind and multiple brain cells to grasp the complexities of DMA cheating.
- Two Computers: While using one PC is possible, it defeats the purpose unless you’re developing DMA cheats.
- Quality Firmware: Be cautious when selecting vendors to ensure you get reliable firmware.
- Kmbox: The kmbox b+ pro is recommended; the kmbox net is considered unreliable.
- Desktop PC: The DMA card plugs into a PCIe slot. Avoid ASUS or Gigabyte motherboards due to known issues.
- Fuser: For a smooth ESP (Extra Sensory Perception) experience, use a fuser. There are several methods available, but they come with a risk of detection.

Choosing the Right DMA Card
DMA cards vary in speed, with different models suited for different needs. The speed is crucial for features that require heavy Write Process Memory (WPM) and Read Process Memory (RPM) operations, such as silent aim or omni sprint. Here’s a breakdown of the available DMA cards:
- 35T Cards:
- Recommended: 35T DMA Card (PCIe)
- Average Speed: 150-200 MBPS
- Pros: Reliable with excellent support.
- 75T Cards:
- Recommendation: 75T DMA Card (PCIe)
- Average Speed: 250-300 MBPS
- 100T Cards:
- Recommended: ZDMA
- Average Speed: 800-1050 MBPS
- Pros: Currently the only source for high-speed boards.
Avoid cheap Chinese DMA cards due to their lack of support and reliability issues compared to Western boards.
Setting Up Your DMA Card
Setting up your DMA card involves several steps to ensure it functions correctly. Here’s a detailed guide (credit to root / James for the original instructions):
- Turn Off Your Main PC: Unplug it to avoid any potential damage.
- Insert the Board: Plug your DMA board into the PCIe slot of your main PC.
- Connect USB Cable: Connect the USB cable from the data port on the DMA to your second PC.
- Boot into BIOS: Start your main PC and boot into BIOS.
- Adjust BIOS Settings: Disable or adjust the following settings:
- Virtualization (Intel)
- VT-d
- Virtualization (AMD)
- IQMMU (AMD CBS > NBIO Common Options > NB Configuration > IOMMU)
- NX-Bit (if available, CPU Settings Secure Virtual Machine)
- Secure Boot (if the option is greyed out, clear all keys)
- Set PCI slot of DMA from Auto to Gen1 (Advanced > PCI Settings)
- Save and Exit BIOS: Boot your main PC into Windows.
- Boot Second PC: Start your second PC and boot into Windows.
- Device Recognition: You should see “FTDI FT601 USB 3.0 Bridge Device” in Device Manager -> Universal Serial Bus controllers on the second PC.
Flashing Firmware to Your DMA Card
Flashing your firmware requires caution and reliable guidance from your firmware provider. Many providers can be unreliable, so ensure they offer thorough support throughout the process.
Download DMA Tools mentioned in below video: https://mega.nz/folder/HwZCxDrD#2C2edLbOT3c_ia5-7KBKbg
Developing for DMA
For those looking to develop DMA cheats, Metick’s DMA wrapper is highly recommended. It includes all the necessary components to create a competent external cheat, including shellcode injection.
Troubleshooting Common Issues
Using a DMA card can come with various challenges. Here are some troubleshooting steps to help you navigate potential problems:
- BSOD (Blue Screen of Death): Often caused by firmware conflicts. Flashing different firmware can resolve these issues.
- Bans: Consult your firmware provider and check for ban waves; it’s typically a firmware issue.
- Bad TLP Requests in Console: This indicates a firmware problem. Contact your provider for a fix.
Conclusion
Navigating the world of DMA cheats involves a combination of technical knowledge, reliable hardware, and quality support. By following this guide, you’ll be better equipped to set up and use your DMA card effectively, maximizing your gaming experience while minimizing risks. Remember, the DMA Custom Firmware you decide to use is critical to successfully staying undetected.
For more detailed discussions and community support, refer to the original guide on Unknown Cheats. Happy cheating!