In the ever-evolving landscape of video gaming, both players and developers continually push the boundaries of technology to enhance performance and experience. However, this technological race also extends to the domain of cheating and anti-cheat mechanisms. One of the most sophisticated tools in the arsenal of cheaters today is the Direct Memory Access (DMA) card. In this blog post, we will explore the origins of DMA cards, their application in video games, and the challenges they pose for current anti-cheat systems.
The Origins of DMA Cards
Direct Memory Access, or DMA, is a feature that allows certain hardware subsystems within a computer to access system memory independently of the central processing unit (CPU). This technology has been integral to computer architecture for decades, originally designed to optimize data transfer processes and improve system efficiency.
DMA technology first emerged in the early days of computing, primarily in mainframes and later in personal computers. It was used to enhance the performance of various peripherals such as hard drives, network cards, and sound cards by allowing these devices to transfer data directly to and from memory without burdening the CPU. This capability significantly improved overall system performance, particularly in tasks that required large data transfers.
The Emergence of DMA Cards in Gaming
In the context of video games, DMA cards have taken on a more nefarious role. Around the mid-2010s, as competitive gaming and eSports gained immense popularity, the incentive for cheating grew substantially. Cheaters began to seek out increasingly sophisticated methods to gain an unfair advantage. DMA cards emerged as a powerful tool in this regard due to their ability to access and manipulate system memory without being detected by traditional software-based anti-cheat measures.
How DMA Cards Work in Gaming
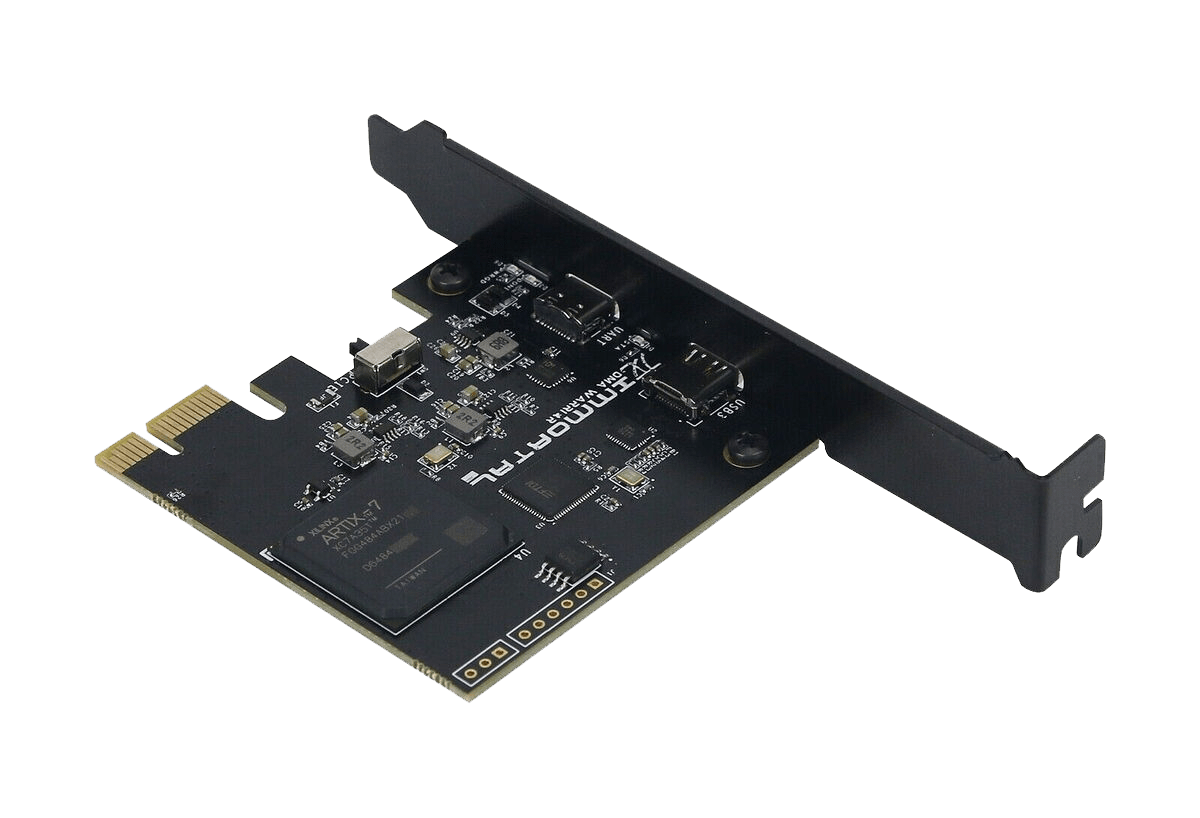
A DMA card typically connects to a computer through an interface such as PCI Express (PCIe). Once installed, it can read and write directly to the system’s memory. Cheaters use DMA cards to read game data, such as player positions, health stats, and other crucial information, which can then be relayed to external devices or displayed as an overlay on the screen. This enables features like wallhacks, aimbots, and other cheats that provide a significant competitive edge.
What makes DMA cards particularly insidious is their ability to operate outside the purview of the operating system. Since they interact directly with the hardware, they bypass many of the security mechanisms that operating systems and anti-cheat programs use to detect malicious activities. This makes them incredibly difficult to detect and counter.
The Challenge for Anti-Cheat Systems
Traditional Anti-Cheat Measures
Most anti-cheat systems employed by game developers rely on software-based methods to detect cheating. These include:
- Signature Scanning: Identifying known cheat software by its digital signature.
- Behavioral Analysis: Monitoring for unusual patterns of behavior that indicate cheating.
- Integrity Checks: Verifying that game files and memory have not been tampered with.
While these methods can be effective against conventional cheats, they struggle to detect the activities of DMA cards. Since DMA cards operate at the hardware level and do not leave typical digital signatures, traditional anti-cheat systems often remain oblivious to their presence.
Hardware-Level Detection
To combat the rise of DMA-based cheating, some developers and anti-cheat companies have begun exploring hardware-level detection methods. These include:
- Telemetry Data: Monitoring the data flow between the CPU and other components to identify unusual patterns indicative of DMA card usage.
- Firmware Checks: Scanning for unauthorized firmware on peripheral devices that could indicate the presence of a DMA card.
- Hardware Fingerprinting: Creating unique identifiers for legitimate hardware to detect any unauthorized modifications or additions.
However, implementing these measures is not without its challenges. Hardware-level detection requires deep integration with the operating system and can pose significant privacy and security concerns. Moreover, the constant evolution of DMA card technology means that anti-cheat systems must continually adapt to new threats.
The Future of DMA Cards and Anti-Cheat Measures
As the cat-and-mouse game between cheaters and developers continues, it is clear that DMA cards represent a significant challenge for the gaming industry. The sophistication and stealth of these devices necessitate equally advanced and multifaceted anti-cheat solutions.
Collaborative Efforts
One promising approach is increased collaboration between game developers, hardware manufacturers, and cybersecurity experts. By sharing information and resources, these stakeholders can develop more robust anti-cheat measures that leverage both software and hardware capabilities.
Machine Learning and AI
Another avenue is the use of machine learning and artificial intelligence to detect cheating behaviors. By analyzing vast amounts of gameplay data, AI algorithms can identify subtle patterns that may indicate the use of DMA cards or other sophisticated cheats. These systems can then adapt and improve over time, providing a more dynamic defense against evolving threats.
Education and Awareness
Finally, educating players about the impact of cheating and promoting a culture of fair play can also help mitigate the problem. Many players who might consider using cheats are unaware of the broader implications for the gaming community and the potential consequences for themselves.
Conclusion
The rise of DMA cards in video gaming is a testament to the relentless pursuit of competitive advantage, but it also highlights the ongoing battle between cheaters and anti-cheat systems. While DMA cards present a formidable challenge, the industry is responding with innovative solutions that combine software, hardware, and AI-driven approaches. As technology continues to evolve, so too will the strategies for ensuring fair and enjoyable gaming experiences for all players. By staying vigilant and adaptive, the gaming community can continue to thrive in the face of these sophisticated threats.